While analyzing XING’s event management platform, I identified a reflected XSS vulnerability in the way event IDs are handled. The vulnerability occurs because the input is improperly sanitized in a JavaScript context, allowing an attacker to inject and execute arbitrary JavaScript by exploiting unsanitized double quotes.
I started by inspecting how event pages are loaded on XING. The following URL is used to display event information:
https://www.xing-events.com/HBKCRJV.htmlThe event ID (HBKCRJV) is dynamically inserted into a JavaScript snippet:
iframeVWO.src = "https://vwo.xing-events.com/HBKCRJV.html?language=de";While the application properly sanitized special characters like < and >, double quotes (") were not handled correctly. This allowed me to inject a malicious payload.
I tested the following payload to confirm the vulnerability:
"-alert(1)-"This resulted in the following URL:
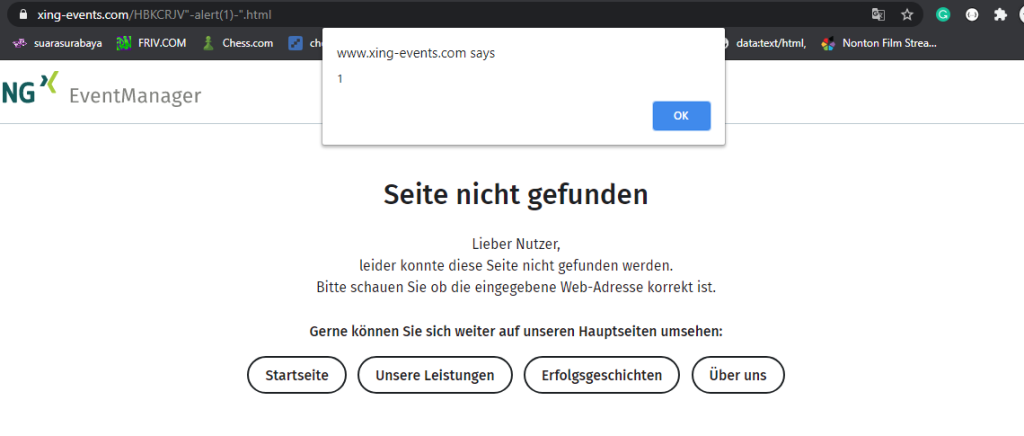
https://www.xing-events.com/HBKCRJV%22-alert(1)-%22.htmlWhen accessing the crafted URL, the malicious payload was reflected in the JavaScript code:
iframeVWO.src = "https://vwo.xing-events.com/HBKCRJV"-alert(1)-".html?language=de";This broke out of the original JavaScript string, allowing the injected payload (alert(1)) to execute.
To reproduce the XSS vulnerability, open the following URL in a browser:
https://www.xing-events.com/HBKCRJV%22-alert(1)-%22.htmlThis triggers the injected JavaScript payload, demonstrating the vulnerability.
Timeline
- 22/12/2020: Report submitted.
- 22/12/2020: Vulnerability triaged.
- 22/12/2020: Bounty of $300 awarded.
- 26/01/2021: Bug fixed.
This issue highlights the importance of properly sanitizing all user inputs, especially when they are reflected in a JavaScript context. Ensuring that all characters, including double quotes, are properly escaped can prevent similar vulnerabilities.




Leave a Reply