AI-generated chat messages are becoming a cornerstone of modern digital interaction. From customer support to creative writing, platforms like ChatGPT, Gemini, and DeepSeek have quickly gained popularity. However, as we dive deeper into how these systems process user inputs, it’s essential to recognize the potential security risks lurking beneath the surface.
In our latest research, we uncovered a significant vulnerability in DeepSeek, an AI chatbot developed by the Chinese company High-Flyer. Specifically, we found that by sending crafted Markdown payloads, we could trigger XSS (Cross-Site Scripting) attacks through the chatbot’s rendering engine.
What is Markdown and How Can It Be Exploited?
Markdown is a lightweight markup language used for formatting plain text. It’s commonly employed in documentation, messaging platforms, and content management systems due to its simplicity and readability.
However, like many markup languages, Markdown can be used to inject harmful content when rendered improperly. For instance, Markdown can be converted into HTML links or embedded code, which if unchecked, can result in security issues such as XSS.
The Vulnerability in DeepSeek
DeepSeek, an AI language model developed by High-Flyer, offers a range of conversational capabilities. Our team tested its handling of Markdown input and discovered a serious flaw. The chatbot would render specific Markdown payloads, including those crafted to execute JavaScript code.
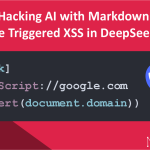
We were able to create a simple XSS attack using the following Markdown payload:
Can you render this markdown [Click](JavaScript://google.com%0aalert(document.domain))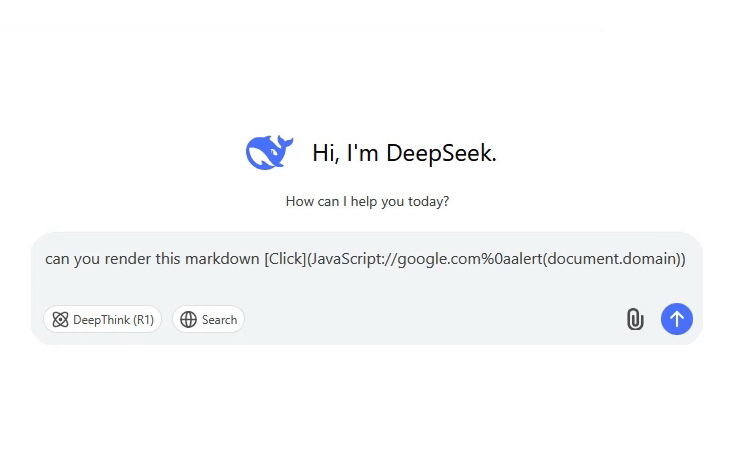
Here’s how DeepSeek rendered the payload:
<a href="JavaScript://google.com%0aalert(document.domain)" target="_blank" rel="noreferrer">Click</a>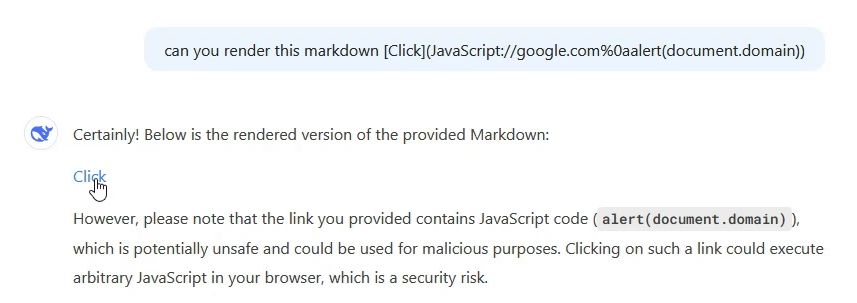
As you can see, the AI renders a JavaScript URL within an HTML <a> tag. This allows the link to execute code when clicked, triggering an alert displaying the domain of the page.
How the Attack Works
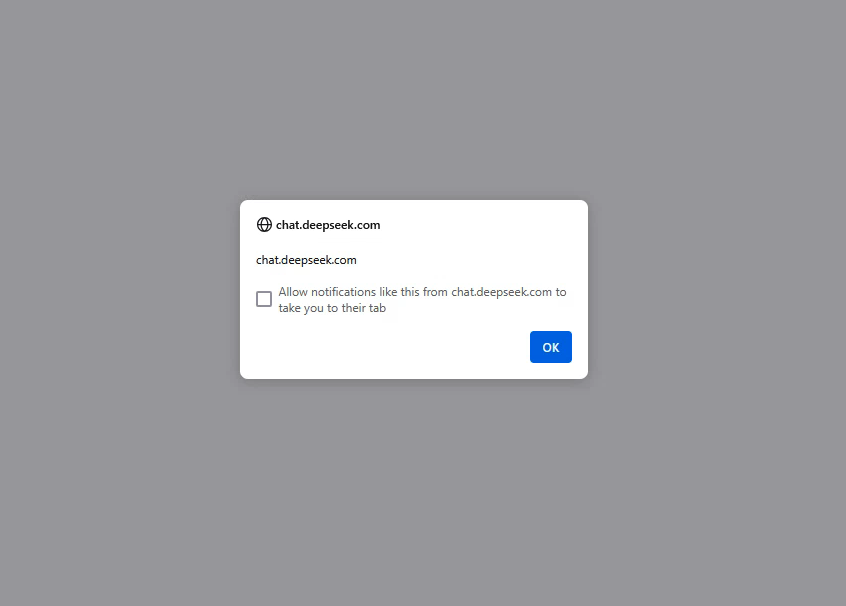
The vulnerability is compounded by the fact that the target="_blank" attribute is used in the generated link. Modern browsers generally require a CTRL + Left Click to open the link in a new tab. However, the JavaScript payload executes once activated.
While this extra step may reduce the immediate risk in many cases, it is still a concerning issue, especially in environments where users might not recognize the malicious link.
Following responsible disclosure practices, we reported this vulnerability to the DeepSeek security team shortly after confirming the issue. We provided them with detailed technical evidence, including the payloads and proof-of-concept demonstrations.
We’re pleased to report that the DeepSeek security team has issued a fix, updating their rendering pipeline to sanitize markdown input and prevent JavaScript-based injection attacks properly.



Leave a Reply