During my recent bug bounty hunting, I started by gathering information on the Microsoft domain using a simple Google Dork query to locate potentially vulnerable pages. The search query I used was:
site:*.*.microsoft.com ext:php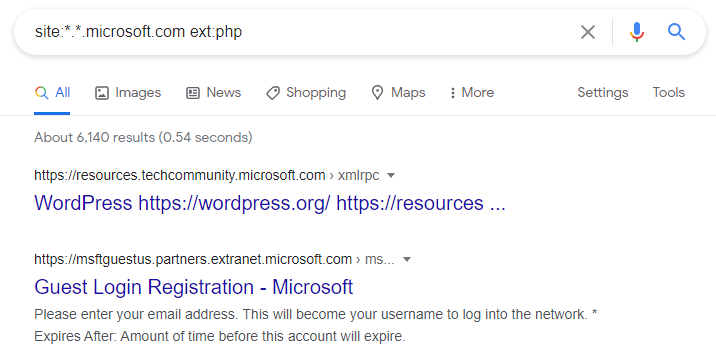
This helped me identify pages on Microsoft’s domain that had the .php extension. After reviewing the results, I came across a specific URL that seemed interesting:
URL:
https://msftguestus.partners.extranet.microsoft.com/guest/msft_a_guest_register.php?_browser=1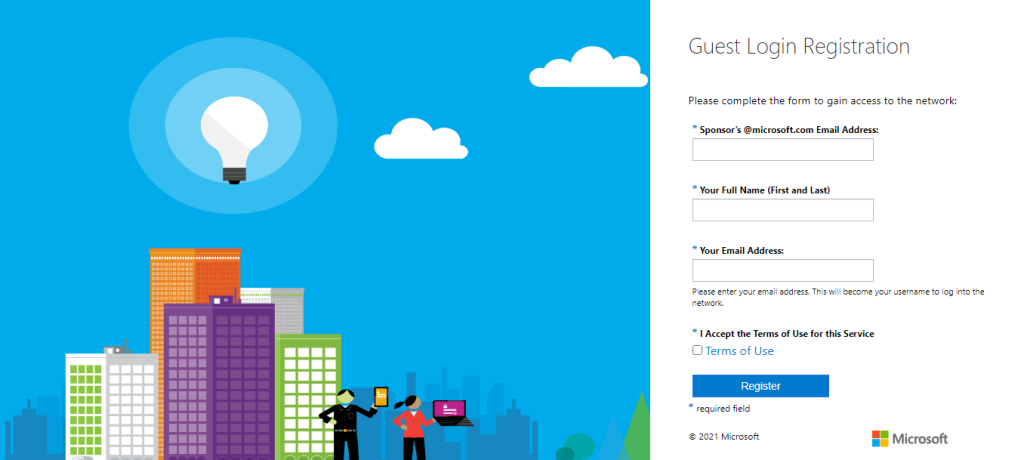
At this point, I decided to dig deeper into the parameters on the page. To accomplish this, I used a tool called Arjun. Arjun is an effective tool for discovering hidden parameters in web applications, and it helped me identify all the parameters that were being passed in the URL.
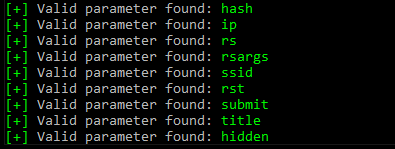
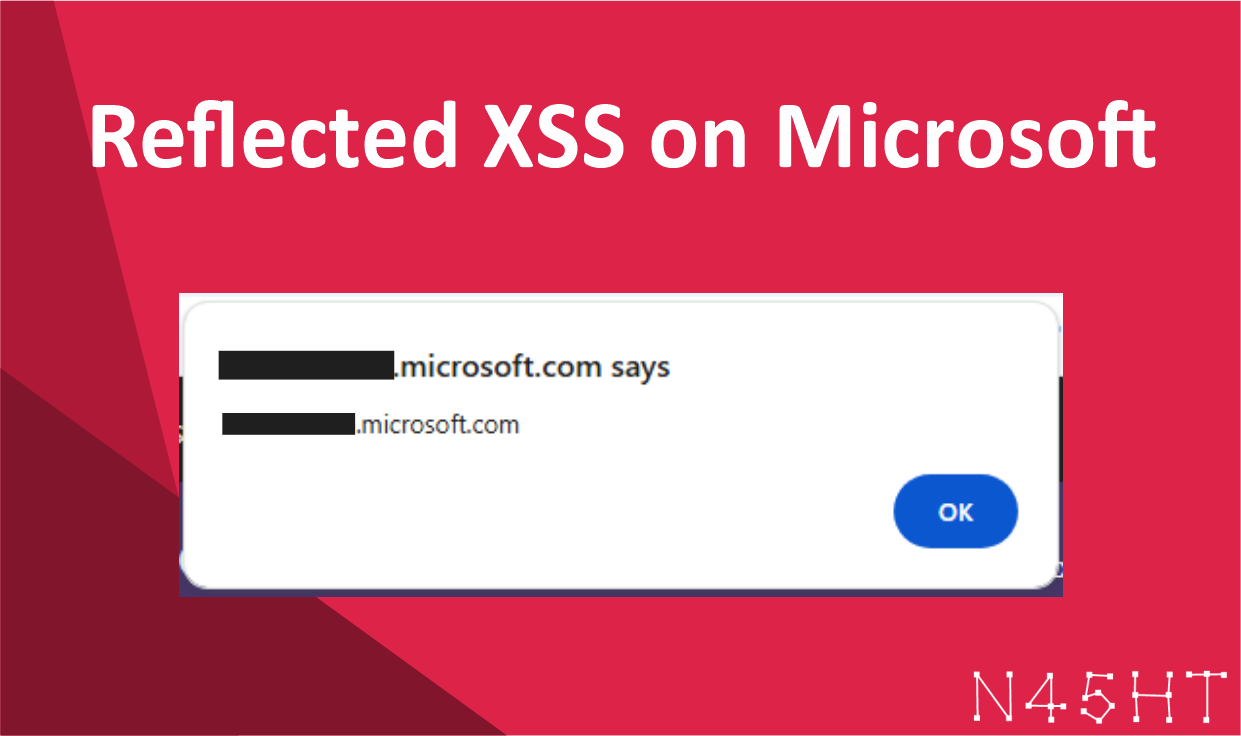
Once I had the parameters, I tested each one by injecting various XSS payloads to check for any Cross-Site Scripting (XSS) vulnerabilities. I started with a simple but effective payload:
"><svg/onload=alert(1)>This payload triggers an alert box when the page is loaded, and after testing it on one of the parameters, the XSS vulnerability successfully triggered, confirming the presence of an XSS flaw.
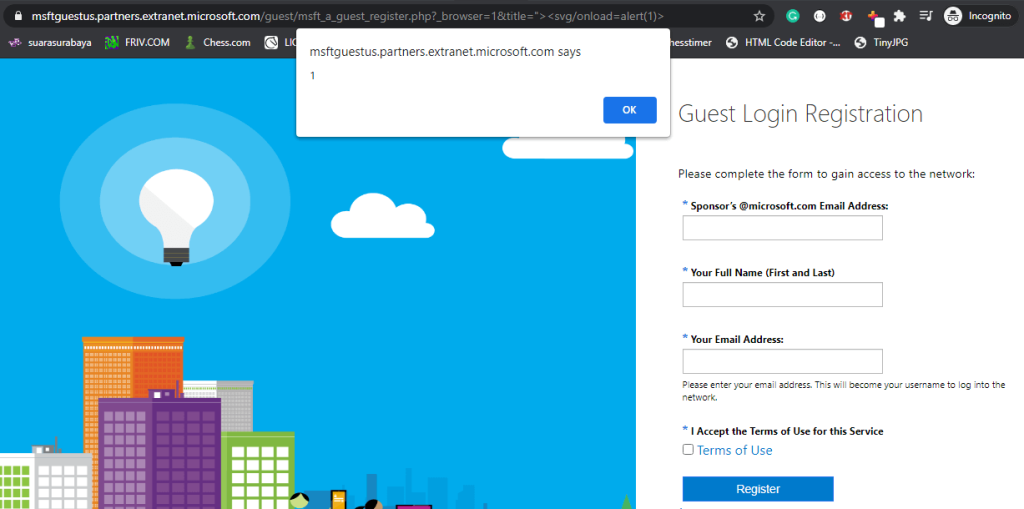
This vulnerability could potentially allow attackers to execute malicious scripts in the context of another user’s session, which could lead to a variety of security risks such as session hijacking or information theft. I’ve reported this issue responsibly, and I hope it gets patched soon.
#HappyHacking



Leave a Reply