-

Reflected DOM-based XSS on DomaiNesia
•
In this article, I’ll walk you through how I discovered a Reflected DOM-based Cross-site Scripting (XSS) vulnerability on…
-

Exploiting XSS via Markdown on Xiaomi
•
Markdown is a popular text-to-HTML conversion tool, commonly used in forums and web platforms to create web content.…
-

N45HT Vulnerability Disclosure Program
•
No technology is perfect, and N45HT believes that working with skilled security researchers across the globe is crucial…
-
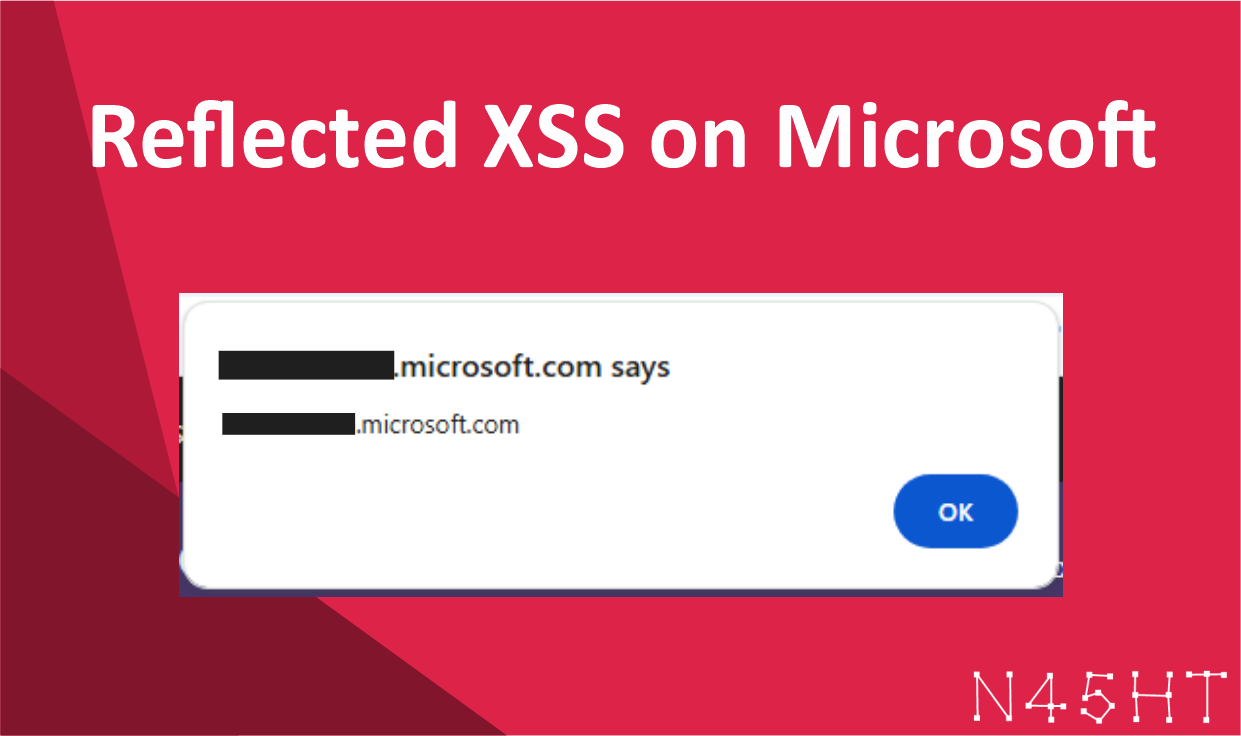
Reflected XSS on Microsoft
•
During my recent bug bounty hunting, I started by gathering information on the Microsoft domain using a simple…
-

XSSR: An automatic XSS scanner
•
Is an automatic Cross-site Scripting scanner application with Website, Chrome Extensions, and Windows Desktop platforms. Get in touch:
-

$300 Bounty for Exploiting DOM-based XSS
•
While analyzing XING’s event management platform, I identified a reflected XSS vulnerability in the way event IDs are…
-
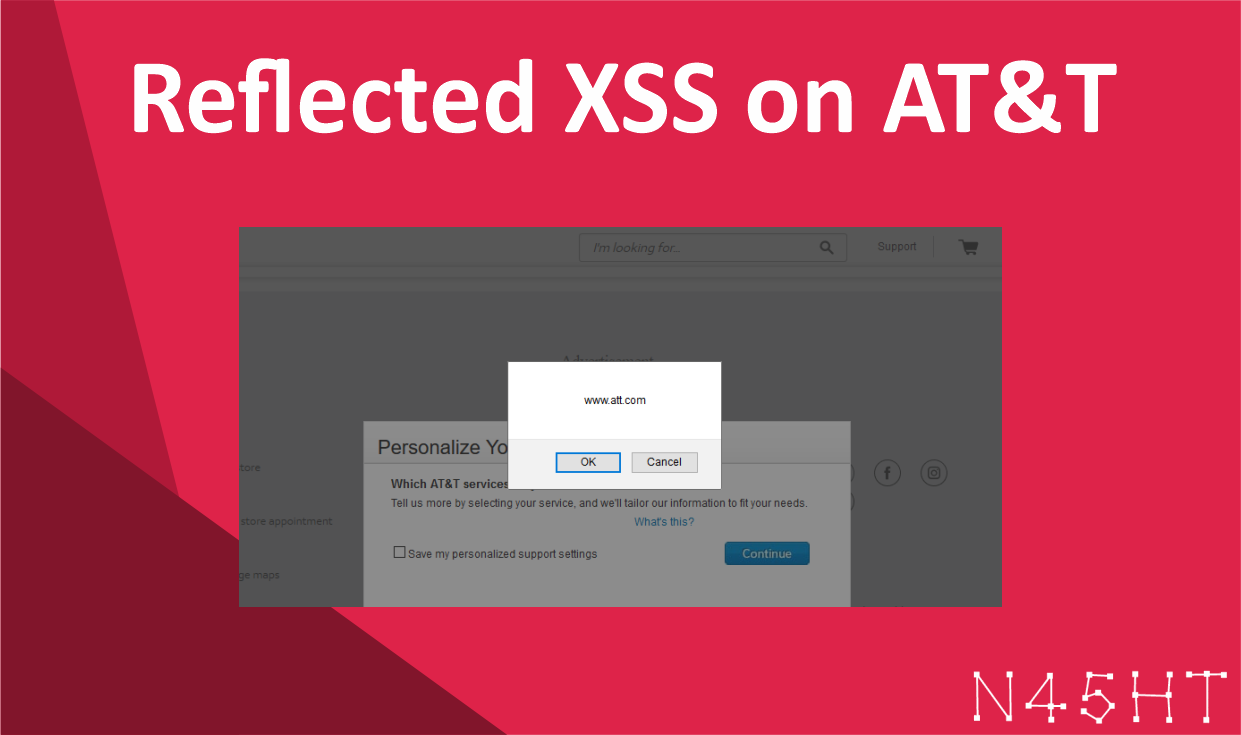
Reflected XSS on AT&T
•
While performing a Google Dork search for potential vulnerabilities, I used the following query to target AT&T’s website:…
-
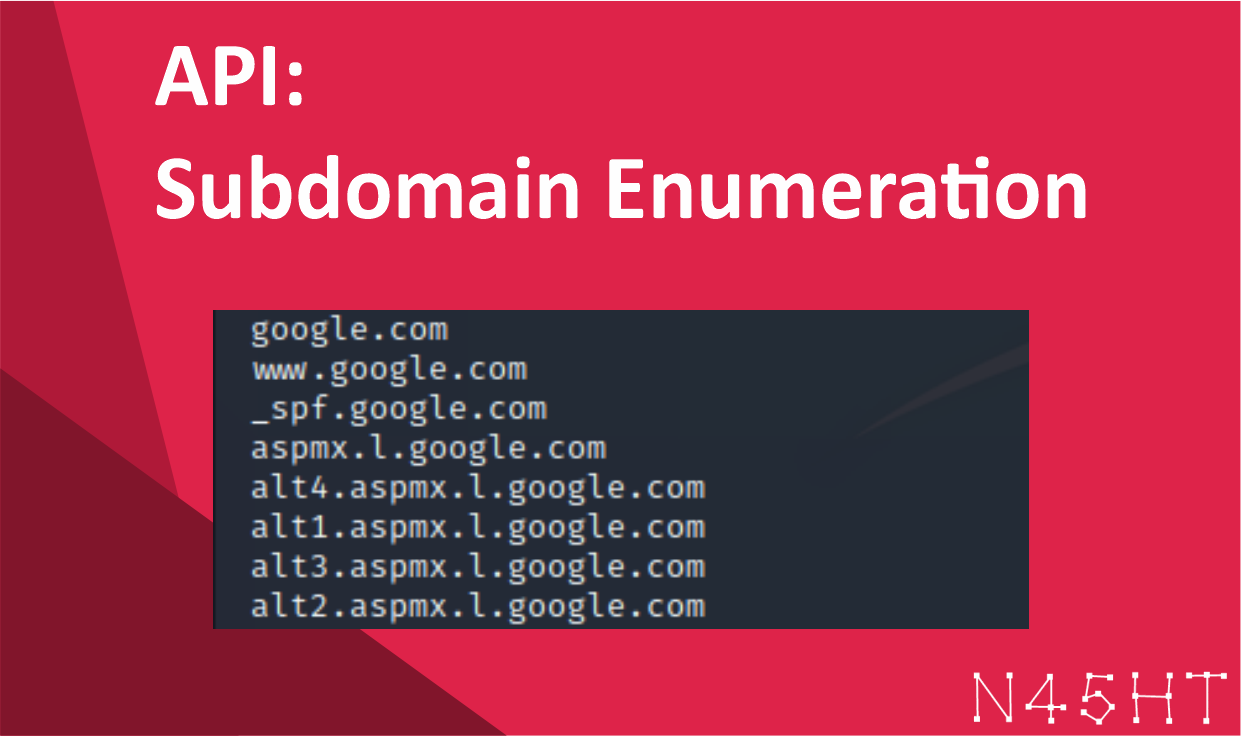
API: Subdomain Enumeration
•
Subdomain Enumeration is the process of finding sub-domains of a domain, this is an important phase in a…
Recent Posts
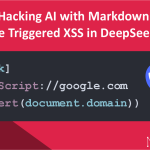
- Hacking AI with Markdown: How We Triggered XSS in DeepSeek’s ChatAI-generated chat messages are becoming a cornerstone of modern digital… Read more: Hacking AI with Markdown: How We Triggered XSS in DeepSeek’s Chat
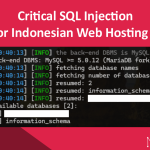
- Critical SQL Injection in a Major Indonesian Web Hosting PlatformWhile exploring vulnerabilities in a major web hosting company in… Read more: Critical SQL Injection in a Major Indonesian Web Hosting Platform
- Breaking Vercel’s Clone URL with a Simple XSS ExploitDuring my exploration of Vercel’s platform, I discovered a reflected… Read more: Breaking Vercel’s Clone URL with a Simple XSS Exploit
- Bypassing Razer’s WAF for XSSWhile testing Razer’s web application, I identified an XSS vulnerability… Read more: Bypassing Razer’s WAF for XSS
- Finding WordPress Vulnerabilities on CarGurus with WPScanWhile exploring CarGurus’ bug bounty program, I discovered a reflected… Read more: Finding WordPress Vulnerabilities on CarGurus with WPScan
Social Media
Advertisement
Tags
API Bug Bounty Capture The Flag Cross-site Scripting CTF ExifTool HTML JavaScript Markdown Open Redirection PHP SQL Injection VDP WAF Web Application Firewall XSS XSSR XSSRush