httpstatus.io is a tool that allows you to check HTTP status codes, headers, and redirects. For example, when you submit a URL or domain, httpstatus.io will check the HTTP status code and where the domain will be redirected, such as when the HTTP status code is 301, 302, etc.
Let me walk you through an interesting scenario I explored with httpstatus.io.
Step-by-Step Exploit:
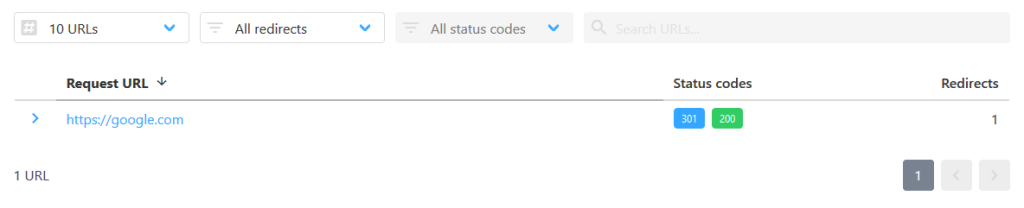
I started by submitting a normal URL, for example:
https://google.comThe response was normal, as expected.
Next, I decided to submit a domain without a protocol:
google.comThe server automatically added the protocol (either HTTP or HTTPS) to the domain and turned it into:
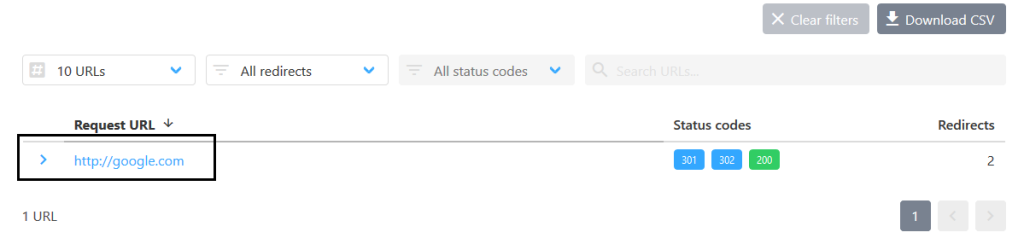
protocol://google.com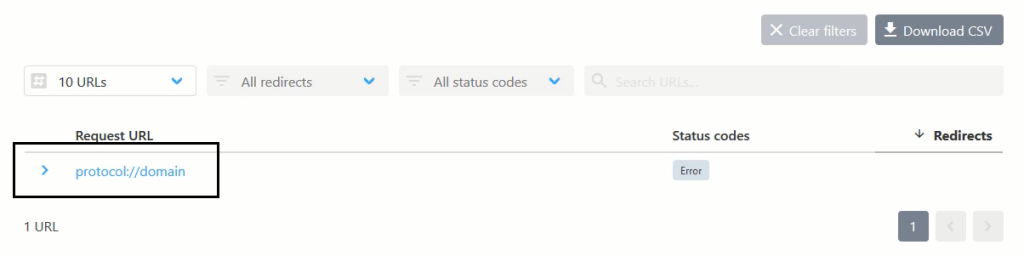
At this point, everything seemed normal, and the server treated the domain like a regular URL. However, I noticed something interesting when I sent a specific payload instead of a typical URL.
I used JavaScript as the protocol and crafted an XSS payload as the domain. The resulting payload looked like this:
javascript://%0aalert(document.domain);//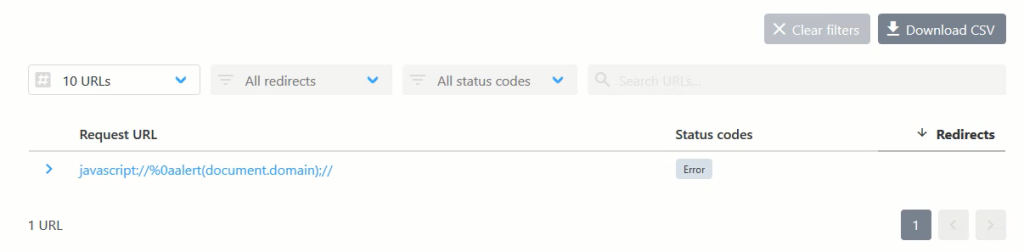
When clicking the resulting link, a window dialog popped up with an alert, executing my JavaScript payload.
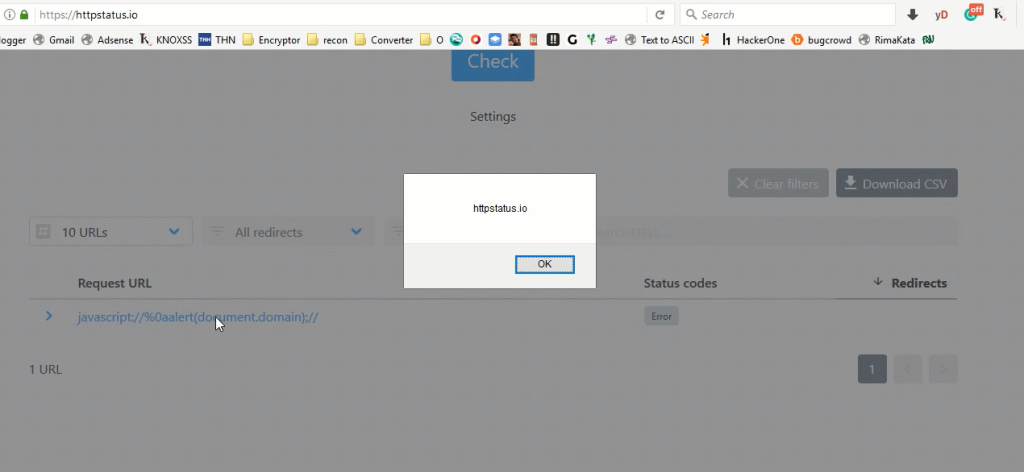
By exploiting how httpstatus.io handles the protocol and domain input, I was able to trigger an XSS vulnerability. This technique relies on the server treating JavaScript as a protocol and the payload as the domain, ultimately executing a script when the URL is clicked.




Leave a Reply