In this article, I’ll walk you through how I discovered a Reflected DOM-based Cross-site Scripting (XSS) vulnerability on the DomaiNesia website using BurpSuite. DOM-based XSS vulnerabilities occur when malicious scripts are executed as a result of user input being reflected directly in the Document Object Model (DOM) without proper sanitization or escaping.
Step 1: Scanning the Target
To begin, I opened BurpSuite and configured it to scan the DomaiNesia website. BurpSuite is a powerful web vulnerability scanner that helps identify potential security issues on web applications. I started by navigating to the Burp Scanner tab and running a scan on the target domain: domainesia.com.
Initial Scan: After a few moments of scanning, BurpSuite displayed an alert showing a potential Cross-site Scripting (XSS) vulnerability on the website.
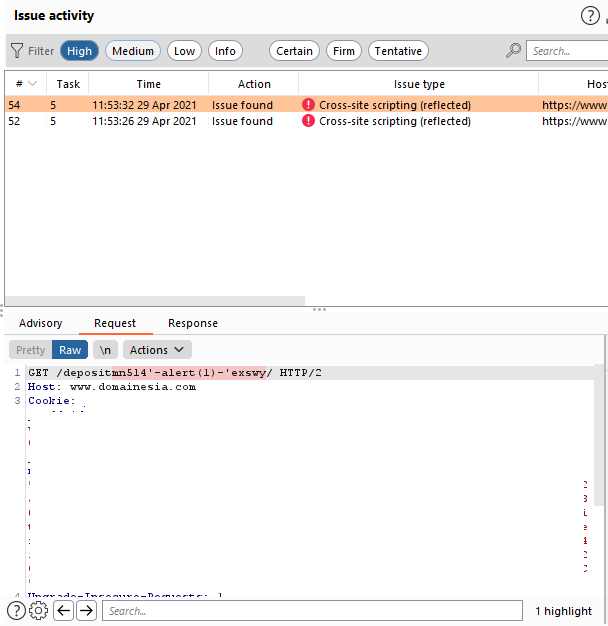
Step 2: Reviewing the XSS Vulnerability
BurpSuite’s scanner provided detailed information about the vulnerability, including the affected page and the nature of the XSS issue. The vulnerability was identified as a Reflected DOM-based XSS, meaning that user input (such as URL parameters) was being reflected in the page’s DOM and executed as JavaScript without being properly sanitized.
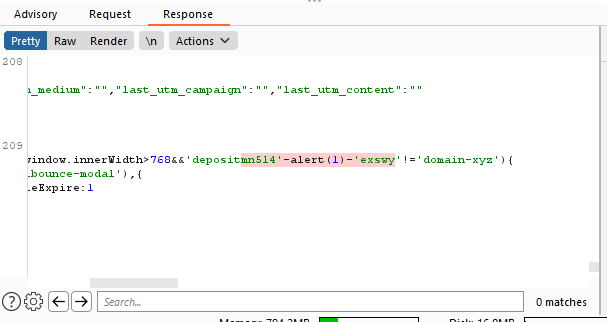
Step 3: Server Response
Here’s the response I received from the DomaiNesia server. It confirmed that user input was being reflected back to the browser without proper escaping or validation, creating the opportunity for XSS attacks.
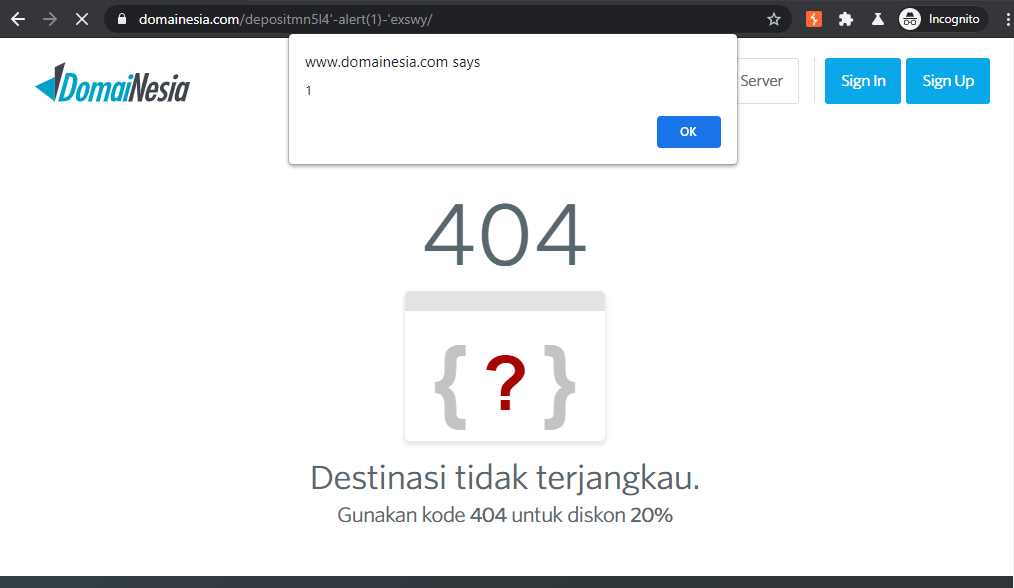
Step 4: Testing the Vulnerability
To test the vulnerability further, I opened the URL directly in my browser. This helped me confirm that the XSS was indeed reflected in the DOM when the page was loaded with a malicious payload in the URL. This means that any user who visits the URL with the payload could have JavaScript executed in their browser, potentially leading to session hijacking, phishing attacks, or data exfiltration.
By using BurpSuite’s scanning features and manually validating the response, I was able to identify and confirm the Reflected DOM-based XSS vulnerability on DomaiNesia. This type of vulnerability is critical because it allows attackers to inject arbitrary JavaScript into a page, which can then be executed in the context of other users’ browsers.
I have reported the issue to the DomaiNesia team, and I hope they address it promptly to improve the security of their platform.
#HappyHacking




Leave a Reply