During my testing of AT&T’s common login page, I discovered a reflected XSS vulnerability in the transactionID parameter. The vulnerability occurs due to improper handling of user input, allowing for the execution of malicious JavaScript.
The vulnerable URL is:
https://cprodmasx.att.com/commonLogin/igate_wam/cancel2FAFlow.do?transactionID=dadadaHere, the transactionID parameter is used within the page, which I suspected could be vulnerable to reflected XSS. By testing payloads, I found that this parameter does not sanitize input properly.
I injected a simple XSS payload into the transactionID parameter. The payload was as follows:
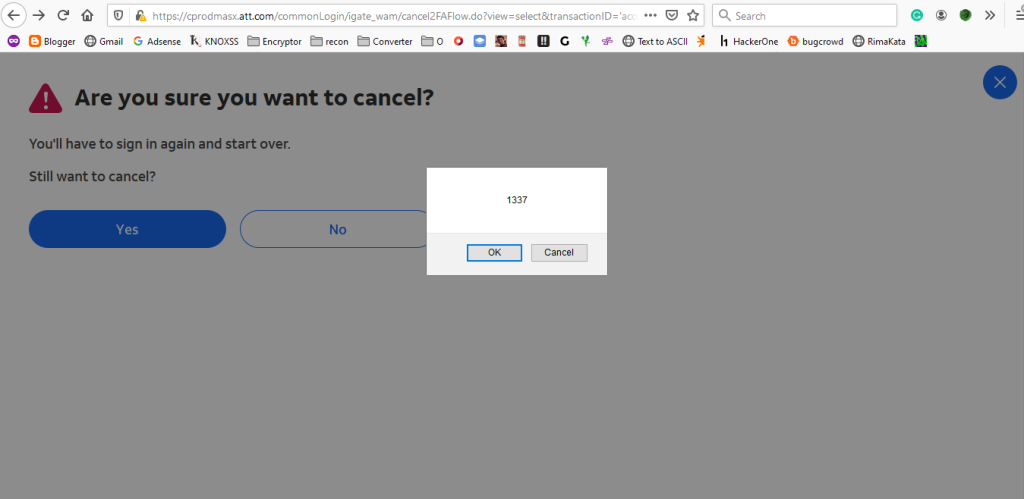
'accesskey='x'onclick='confirm`1337`When inserted into the URL, the payload looked like this:
https://cprodmasx.att.com/commonLogin/igate_wam/cancel2FAFlow.do?transactionID='accesskey='x'onclick='confirm`1337`To trigger the XSS, I used keyboard shortcuts to activate the payload.
- Windows: Press
ALT + SHIFT + X - OS X: Press
CTRL + ALT + X
This causes the payload to execute, showing a confirmation dialog with the message 1337.
#HappyHacking



Leave a Reply