Yesterday, I discovered a Stored Cross-Site Scripting (XSS) vulnerability on the Xiaomi Forum via Markdown. Today, I’ve found another critical vulnerability: a Stored DOM-based XSS issue on the same platform. In this writeup, I will walk you through how I found this vulnerability and demonstrate how it can be exploited.
Related Posts:
For those interested, here’s a related writeup on how I exploited an XSS vulnerability via Markdown on Xiaomi Forum:
To begin, I tried to post a thread on the Xiaomi Forum to see if the input fields were vulnerable to JavaScript execution. I filled out the necessary fields and submitted the thread.
After posting the thread, I immediately inspected the page source to identify any areas where JavaScript might be reflected or executed.
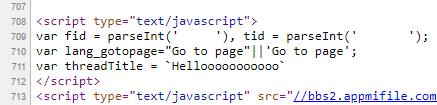
In the source code, I found that the thread title was being displayed inside backticks (`), which is a template literal syntax in JavaScript. Upon further inspection, I realized that DOM-based XSS could be triggered in this context.
The backquote (`) in JavaScript is part of template literals, and it allows us to embed expressions inside a string using the ${} syntax. This means we could inject JavaScript functions directly into the thread title.
Here’s an example of how we can exploit this:
Example:
var abc = `dadada${alert(1)}`In this example, the alert(1) function would be executed, displaying an alert box in the browser. This proves that any JavaScript function inside the ${} syntax within backticks can be executed.
Now, I crafted a malicious payload that would execute an XSS attack when the thread title was displayed on the forum. The final payload I used was:
Payload:
Hellooooooooooo${alert(1)}By injecting this payload into the thread title, I was able to trigger the JavaScript execution as soon as the title was rendered on the page.
When the thread was displayed with my crafted title, the XSS was successfully triggered. The alert box popped up, confirming that the vulnerability existed and was exploitable.
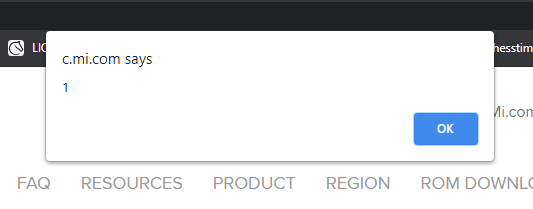
Here’s the response I received from the Xiaomi Forum’s server. The thread title was reflected back into the DOM without any sanitization or escaping, which allowed the injected JavaScript to execute.
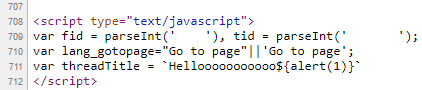
This Stored DOM-based XSS vulnerability in the Xiaomi Forum is a serious security risk because it allows an attacker to inject arbitrary JavaScript into the page, which can then be executed in the context of other users’ browsers. This could potentially lead to various attacks, including session hijacking, phishing, or malicious actions.
I’ve responsibly reported this vulnerability to Xiaomi, and I hope they address it to improve the security of their platform.
#HappyHacking




Leave a Reply