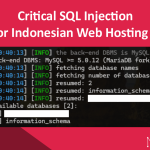
I recently registered on Chess24.com and, after playing a few games, decided to conduct a quick security analysis on the website. I focused on the profile settings page to test for potential vulnerabilities.
XSS Payload Injection
Without wasting much time, I tested a common XSS payload by adding it directly to my profile settings page.
Injected Payload:
https://site.com/?"/onmouseover="alert(1)This was my first attempt at injecting the payload into the URL.
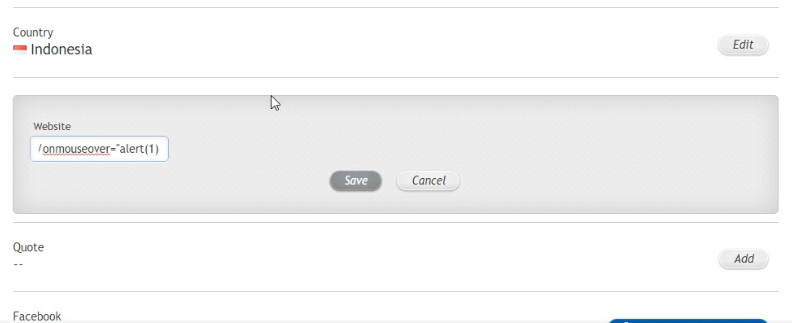
After saving the XSS payload in my profile settings, I checked the source code of the page. The injected payload was reflected in the HTML source as follows:
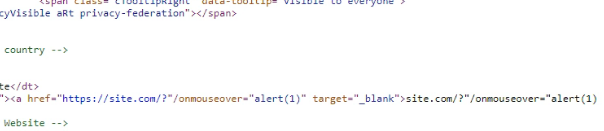
Source Code (After Saving):
<a href="https://site.com/?"/onmouseover="alert(1)">https://site.com/?"/onmouseover="alert(1)</a>This indicated that the website was not properly sanitizing or escaping user inputs, making it vulnerable to stored XSS.
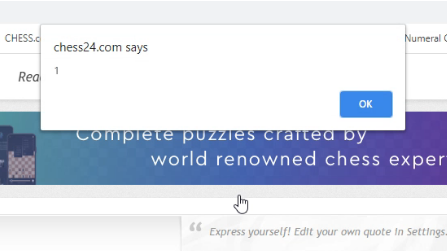
Stored XSS Triggered
As expected, after visiting the page where the payload was stored, I was able to trigger the stored XSS. The payload was executed successfully, showing an alert box.
#HappyHacking




Leave a Reply