In this article, we will share how we successfully bypassed the CloudFront WAF (Web Application Firewall) to exploit a Cross-Site Scripting (XSS) vulnerability.
Payloads:
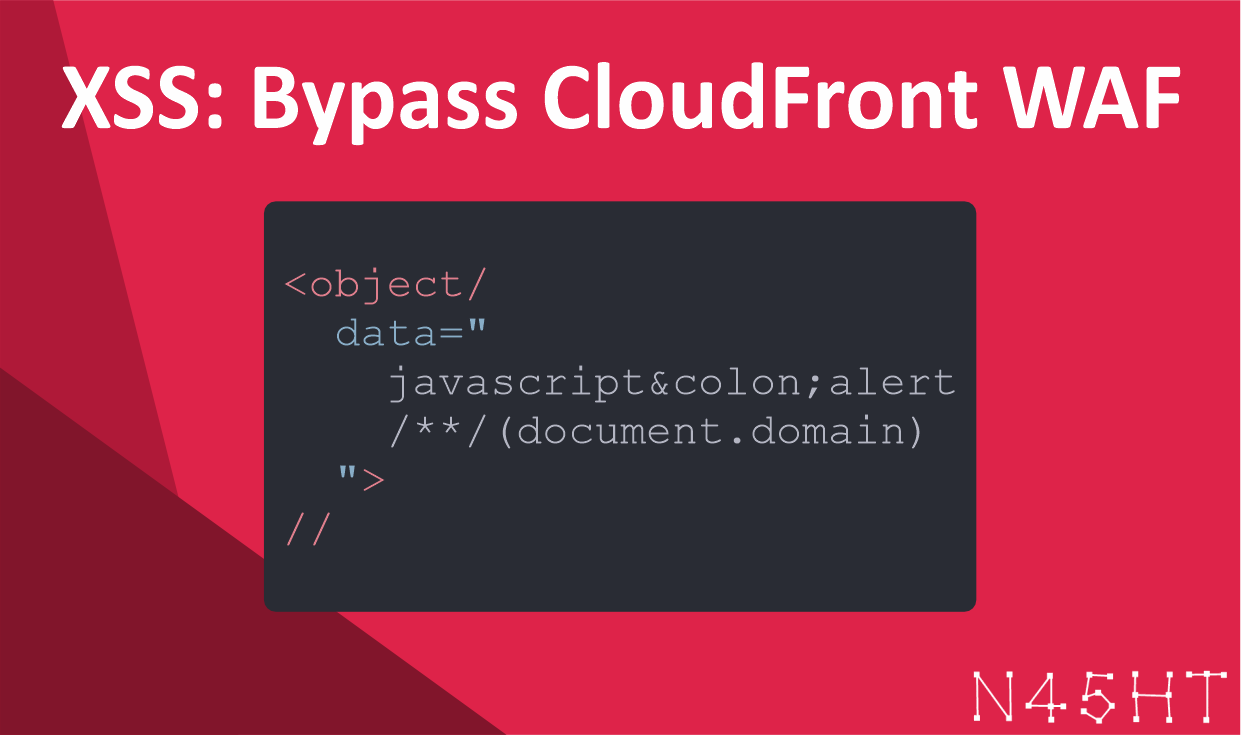
To bypass the CloudFront WAF, we crafted a special XSS payload. The goal was to find a way to inject JavaScript while preventing the WAF from detecting it as malicious. Here is the payload we used:
<object/data="javascript:alert/**/(document.domain)">//</object>This payload is interesting because it uses a combination of an <object> tag and a javascript URI scheme. Notice how the colon (:) in javascript: is encoded as :, which can help bypass basic filtering rules in the WAF. Additionally, the /**/ is used to comment out portions of the string, making it harder for the WAF to detect the attack.
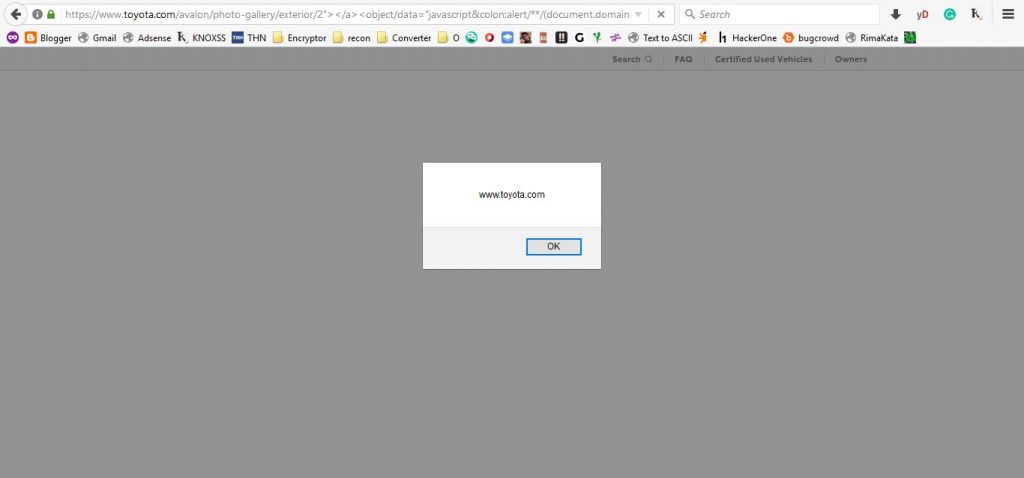
After injecting the payload, we successfully triggered the XSS attack. The CloudFront WAF was bypassed, and the alert box displayed the document’s domain. This confirmed that the vulnerability existed and that the WAF didn’t block our payload.



Leave a Reply