Markdown is a popular text-to-HTML conversion tool, commonly used in forums and web platforms to create web content. It allows users to write HTML in a simplified and easy-to-read format. While it’s a convenient tool, if not properly sanitized, it can open up vulnerabilities, such as Cross-Site Scripting (XSS), which can be exploited by attackers to inject malicious code into a web application.
In this writeup, I found an XSS vulnerability in the comments section of the Xiaomi Forum (c.mi.com), which allowed me to inject JavaScript through Markdown image tags. Here’s the process I followed to identify and test the vulnerability:
Step 1: Initial Test with Image Tag I began by attempting to post an image in the comments section using a standard Markdown image tag:
Payload:
[img]https://server/image.jpg[/img]Response:
<img src="https://server/image.jpg" />At this point, the image was displayed normally in the comments section, confirming that the Markdown was being converted into HTML without any issues. The application wasn’t sanitizing the inputs at this stage, which could lead to potential security risks.
Step 2: Testing with Double Quotes Next, I tried injecting double quotes after the image URL, which is a common tactic to test for input sanitization:
Payload:
[img]https://server/image.jpg"[/img]Response:
<img src="https://server/image.jpg"" />As you can see, the double quote was included in the response, but the server did not sanitize it. This showed that it was still vulnerable to further manipulation with additional payloads.
Step 3: Inserting JavaScript Event Handler Next, I attempted to inject a JavaScript event handler into the image tag by adding the onmouseover attribute, which is commonly used to execute JavaScript when the user hovers over an element:
Payload:
[img]https://server/image.jpg"onmouseover=[/img]Response:
<img src="https://server/image.jpg%22onmouseover=" />However, the server immediately encoded the double quote (") into %22, preventing the JavaScript event handler from being executed. Despite this, the server still allowed the insertion of other potentially dangerous content, which was a step forward in exploiting the vulnerability.
Step 4: Using Uppercase in Event Handler To bypass the encoding, I tried using a mixed-case version of the event handler attribute, since sometimes case sensitivity can evade filters:
Payload:
[img]https://server/image.jpg"OnMoUsEoVeR=[/img]Response:
<img src="https://server/image.jpg"OnMoUsEoVeR=" />As expected, the server allowed the mixed-case event handler to be inserted, demonstrating that the input sanitization was insufficient and was unable to handle different case variations.
Step 5: Final Exploit with JavaScript Code Finally, I injected a malicious JavaScript payload that would redirect the victim’s browser to an attacker-controlled site using the window.location property:
Payload:
[img]https://server/image.jpg"OnMoUsEoVeR=window.location="//google.com[/img]Response:
<img src="https://server/image.jpg"OnMoUsEoVeR=window.location="//google.com" />When the image was rendered, the onmouseover event would trigger the redirect to google.com. This is a clear demonstration of an XSS vulnerability, where an attacker can manipulate content on the forum to perform actions like redirecting users or executing arbitrary JavaScript in the victim’s browser.
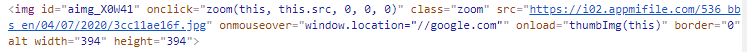
Through this series of tests, I was able to confirm that the Xiaomi Forum’s comment section was vulnerable to Stored XSS due to inadequate sanitization of input within Markdown tags. The vulnerability could be exploited by an attacker to execute JavaScript in the context of a user’s browser, leading to potential phishing attacks, information theft, or session hijacking.
I’ve reported this issue responsibly to Xiaomi, and I hope they address it soon to improve the security of their platform.
#HappyHacking




Leave a Reply