A few days ago, I discovered a Cross-site Scripting (XSS) vulnerability in WinRAR. In this article, I’ll walk you through the steps I took to find this vulnerability and how it works.
What is WinRAR?
WinRAR is a trialware file archiver utility for Windows, developed by Eugene Roshal of win.rar GmbH. It allows users to create and view archives in RAR or ZIP file formats and unpack a variety of other archive formats as well.
For more detailed information, you can check the source on Wikipedia.
Step 1: Observing the WinRAR Behavior
When I first opened WinRAR, I noticed that there was a window that seemed to make an HTTP request to an external web page. This caught my attention, as it could potentially be a vector for injecting malicious code.

Step 2: Capturing the HTTP Request
Immediately, I opened BurpSuite, a popular tool for intercepting and modifying HTTP requests. I used it to capture the requests made by WinRAR when this window was opened.
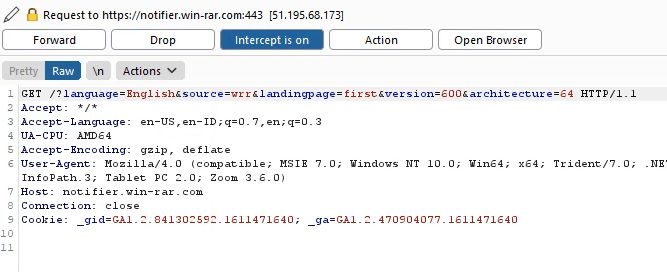
Step 3: Investigating the Request URL
The HTTP request was being sent to the following URL:
https://notifier.win-rar.com/?language=English&source=wrr&landingpage=first&version=600&architecture=64This URL appeared to be related to WinRAR’s notification system, likely sending version and language information to the server.
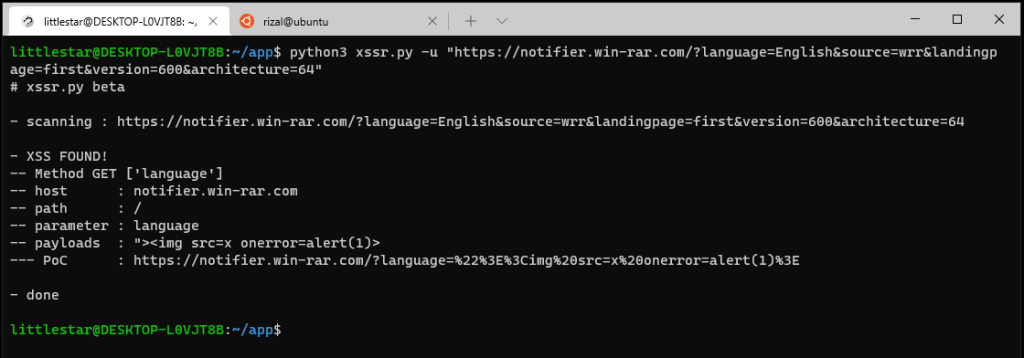
Step 4: Testing for XSS Vulnerability
Curious if the URL was vulnerable to XSS, I decided to run a test using my private XSS Scanner. This tool automatically scans URLs for potential Cross-site Scripting vulnerabilities by inserting common payloads into URL parameters.
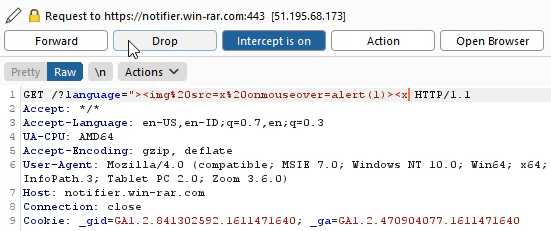
Step 5: Exploiting the XSS Vulnerability via BurpSuite
Next, I manually injected several XSS payloads into the URL using BurpSuite to see if the server would reflect the input without proper sanitization.
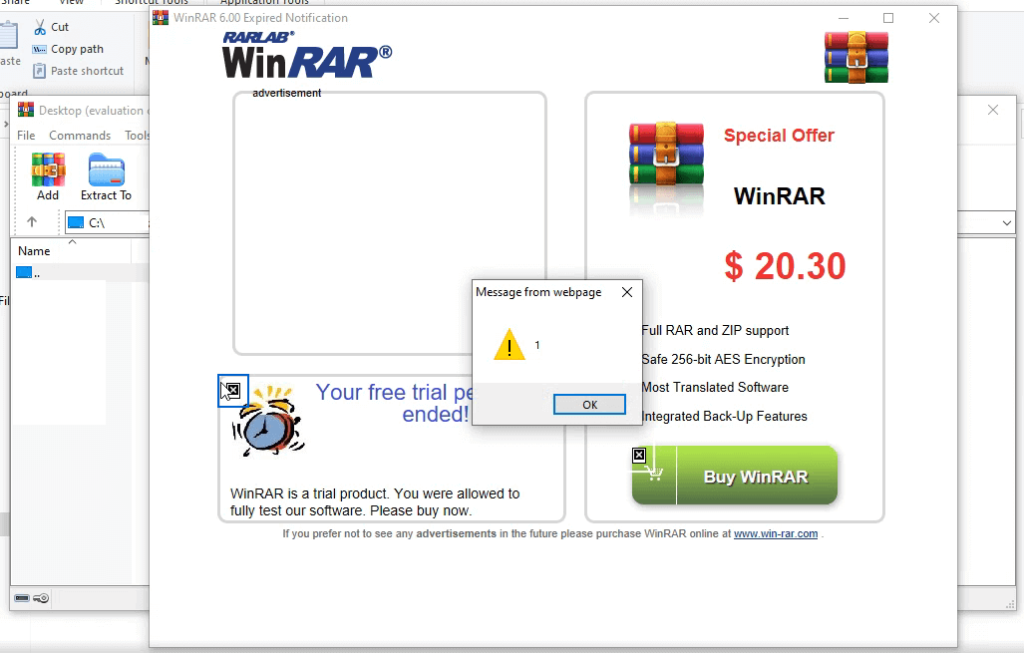
Step 6: XSS Triggered in WinRAR Window
To my surprise, the XSS vulnerability successfully triggered when the payloads were executed. The WinRAR window displayed the injected JavaScript, confirming that WinRAR was vulnerable to Reflected XSS.
Step 7: Demonstrating the Vulnerability (Video PoC)
To provide a clearer demonstration of how the XSS vulnerability works in WinRAR, I created a video proof of concept (PoC). In the video, you can see the XSS payload being triggered and executed within the WinRAR window.
By following these steps, I was able to identify a Reflected XSS vulnerability in WinRAR, which could potentially allow an attacker to execute malicious JavaScript in the context of the application. This type of vulnerability could be exploited for a variety of malicious actions, including stealing user data or compromising the system.
I reported the vulnerability responsibly to the WinRAR team, and I hope they address it promptly to improve the security of the software.
#HappyHacking




Leave a Reply